Okay, so check this out—browser wallets changed how I interact with crypto. Wow! They made swapping and NFT browsing stupidly easy. My instinct said this would simplify things for most users. Initially I thought browser extensions were mostly harmless, but then I ran into a couple of odd edge cases and had to rethink that assumption.
Here’s what bugs me about the ecosystem. Short onboarding flows lure you in. Then permissions prompts pile up and you realize you gave a lot away. Seriously? Yeah. On one hand the UX is incredible; on the other hand the permission model still feels brittle. Actually, wait—let me rephrase that: the UX is great, though the security model is only as strong as the user and the browser. That nuance matters.
I’m biased, but I’m partial to wallets that keep things simple without hiding the tradeoffs. Hmm… somethin’ about an extension that tries too hard to be invisible makes me uneasy. My gut feeling said “trust but verify” after a few interactions with DeFi dapps that requested broad permissions. I clicked ahead once—too fast—and had to undo stuff later. Don’t be me. Learn from my small mistakes.
How to think about a Solana browser extension
Okay, so first—understand the threat model. Short sentence. Browser extensions run in your browser context and can access pages you visit; they can intercept or modify requests. Medium length explanatory stuff that matters a lot. Long thought: when you install a wallet extension you’re effectively granting a piece of software persistent privileges over your web session, which means any vulnerability in that codebase or the extension platform could expose keys, metadata, or transaction intents to risk if the wrong scenario occurs. For an easy first step, always compare the extension publisher name, star ratings, and changelogs to what you expect.
If you want a hands-on starting point, you can check this link: https://sites.google.com/cryptowalletextensionus.com/phantomwalletdownloadextension/ —but be mindful: verify the origin and double-check the store page and official site. Small caveat: I prefer getting extensions from official browser stores, and from links on the official project site, not random third-party pages. This is a good rule of thumb, though not a guarantee.
Practical tip: use a dedicated browser profile for your crypto activity. Short. It isolates cookies and extensions and reduces cross-site leakage. Medium. Longish explanation: by reserving one profile (or even a separate browser) for wallet interactions you cut down on accidental exposures from other extensions you rely on for everyday browsing, which often have far too many permissions for the tasks they’re meant to do.
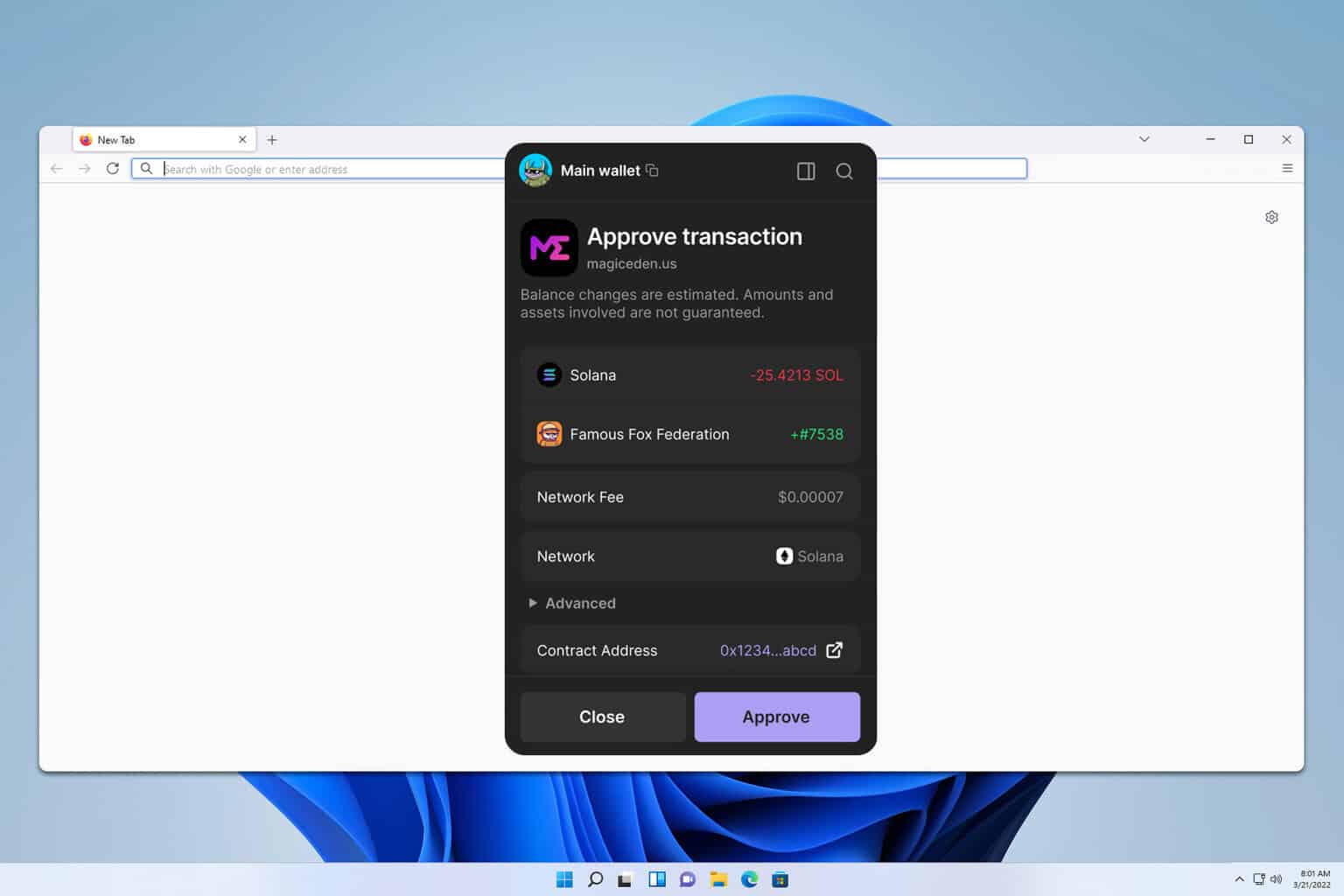
One more quick setup idea—pin the extension so you can see when it’s active. Simple. It keeps you aware. And if a dapp prompts you for a permission you weren’t expecting, pause. Look up the contract or check the transaction details. On a slow analytical note: verify the recipient, the method being called, and the token amounts—transactions are irreversible on-chain, and that matters.
Real tradeoffs I ran into
When I started using Solana extensions, I loved the speed. Transactions felt instant. Whoa! But speed masks complexity. There were moments when a dapp requested signing for a seemingly benign call and the gasless UX made me accept without reading the encoded intent. That part bugs me. On one hand, the experience is frictionless, which is great for adoption; though actually, on the other hand, friction often protects you from mistakes.
Another practical issue: seed backups. Short. Most extensions give you a seed phrase at setup. Medium. Long: if you store that seed phrase in a cloud note or email for convenience, you dramatically increase your attack surface—so either keep it offline in a secure place (preferably a hardware wallet backup) or use a passphrase-protected method with redundancy. I’m not 100% sure everyone’s going to do that, and honestly many people don’t.
Also—extension updates. They can introduce improvements and bugs. Hmm… sometimes an update fixed a UI bug but added a new permission. My impulse is to check release notes, but who reads them? Not me, sometimes. Do take 30 seconds to glance though. Trust but verify, again.
Wallet interoperability is cool. Short. But it also encourages broad approvals across many dapps. Medium. Long thought: signing the same message across multiple sites can create replay or phishing risks if you reuse nonces or if a malicious site tricks you into approving a transaction that looks identical to a legitimate one—so treat signing prompts as you would any legal agreement: read the fine print, or at least pause and confirm the context.
FAQ
How do I know a Solana extension is legit?
Check publisher identity, GitHub repos, official docs, and community channels. Short and to the point. If something smells off—link mismatches, recent negative reports, or weird permission requests—stop. Also, default to official project sites and verified browser stores. I’m biased toward conservative behavior here, but it’s saved me hassle.
Should I use a hardware wallet instead?
Hardware wallets add a strong security layer. Short. They reduce attack surface by keeping keys offline. Medium. Long: for large holdings or long-term storage, use a hardware wallet and connect via the extension only for signing, which limits exposure if the browser environment is compromised—this is the safer tradeoff for serious users.
What if I accidentally approved a bad transaction?
Act fast. Try to cancel pending transactions if the network/tooling allows; change passwords and move remaining funds to a new wallet if you suspect compromise. Hmm… recovery varies by case, and sometimes funds are irrecoverable. Not great. The best defense is prevention—limit approvals and use small test transactions when interacting with new smart contracts.
